TripleTech Project

Infrastructure Modernization Project by RECHNER DATEN TECHNIK INC.
📠Structured Cabling Data & Voice
🚨Firewall & Security
📂AD Server + O365
💿Software Licensing
👁️🗨️Managed Services & Support

Infrastructure Modernization Project by RECHNER DATEN TECHNIK INC.



📠Structured Cabling Data & Voice
🚨Firewall & Security
📂AD Server + O365
💿Software Licensing
👁️🗨️Managed Services & Support

Perform targeted extractions of Apple & Android devices with the Checkra1n exploit or by other means. Get critical data in ten minutes or less, with data from the most popular apps such as WhatsApp, WeChat, Facebook Messenger and others.
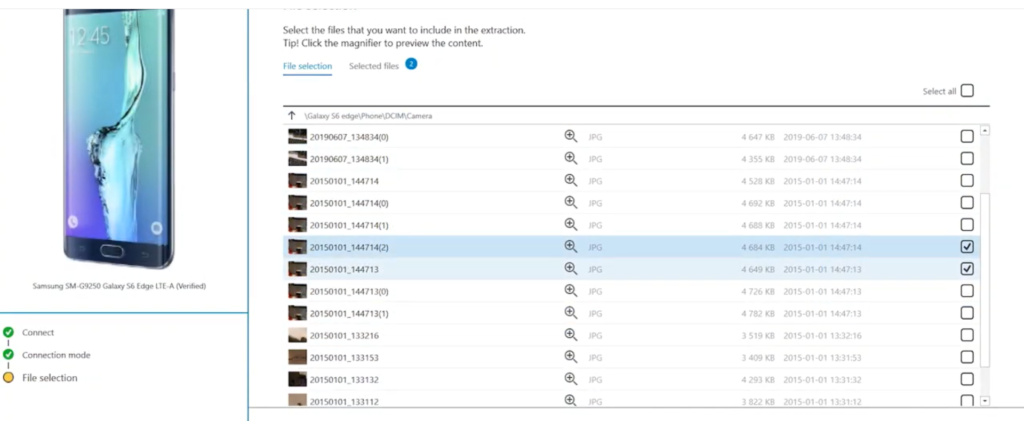
Logical is a rapid extraction method to access and recover live and file system data from the device right on the crime scene, by communicating directly with the operating system of the device.

Physical lets examiners sidestep the operating system to dump all system and deleted data out of the device, plus it also allows you to overcome security and encryption challenges on locked devices.
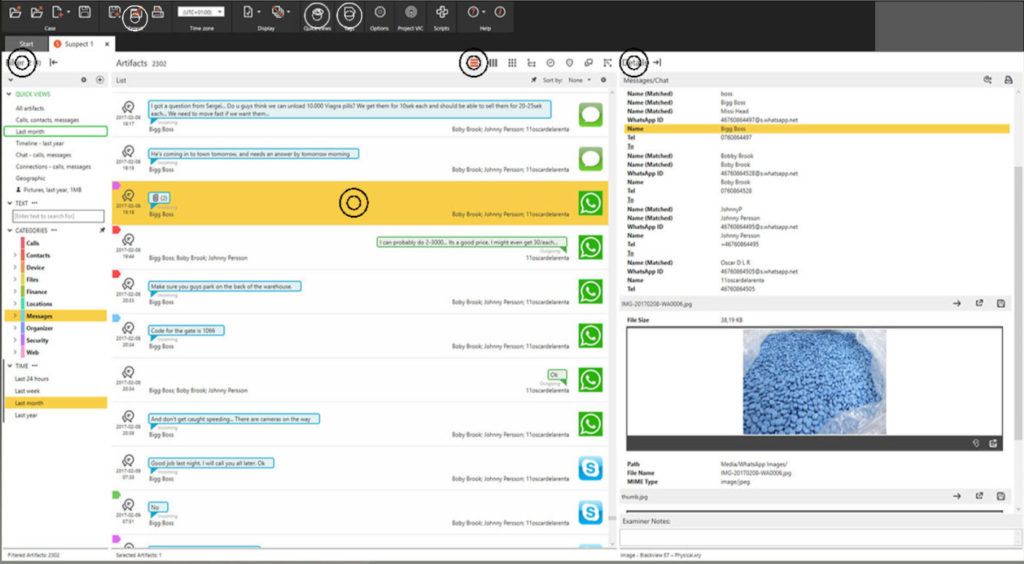
The amount of data stored on mobile phones and other mobile devices is dramatically greater today than ever before. That makes the challenges of searching, filtering and analyzing that data more daunting as well. You need to quickly find what you are looking for, even in huge data sets. Whether your mission is to gather and report intelligence, prevent crime or quickly produce solid evidence

Red Hat Enterprise Linux is a Linux distribution developed by Red Hat for the commercial market. Red Hat Enterprise Linux is released in server versions for x86-64, Power ISA, ARM64, and IBM Z, and a desktop version for x86-64.

Microsoft Corporation is an American multinational technology company with headquarters in Redmond, Washington. It develops, manufactures, licenses, supports, and sells computer software, consumer electronics, personal computers, and related services.

VMware provides cloud computing and virtualization software and services. It was one of the first commercially successful companies to virtualize the x86 architecture.

Surveillance is the monitoring of behavior, activities, or information for the purpose of influencing, managing or directing. This can include observation from a distance by means of electronic equipment, such as closed-circuit television (CCTV), or interception of electronically transmitted information, such as Internet traffic. It can also include simple technical methods, such as human intelligence gathering and postal interception.
Platform as a service (PaaS) or application platform as a service (aPaaS) or platform-based service is a category of cloud computing services that provides a platform allowing customers to develop, run, and manage applications without the complexity of building and maintaining the infrastructure typically associated with developing and launching an app.

Infrastructure as a service (IaaS) are online services that provide high-level APIs used to dereference various low-level details of underlying network infrastructure like physical computing resources, location, data partitioning, scaling, security, backup etc. A hypervisor, such as Xen, Oracle VirtualBox, Oracle VM, KVM, VMware ESX/ESXi, or Hyper-V, LXD, runs the virtual machines as guests. Pools of hypervisors within the cloud operational system can support large numbers of virtual machines and the ability to scale services up and down according to customers’ varying requirements.

Certified Engineers responsibilities includes schedule preparation, pre-planning and resource forecasting for engineering and other technical activities relating to the project. They may also in charge of performance management of vendors. They ensure projects are completed according to project plan.